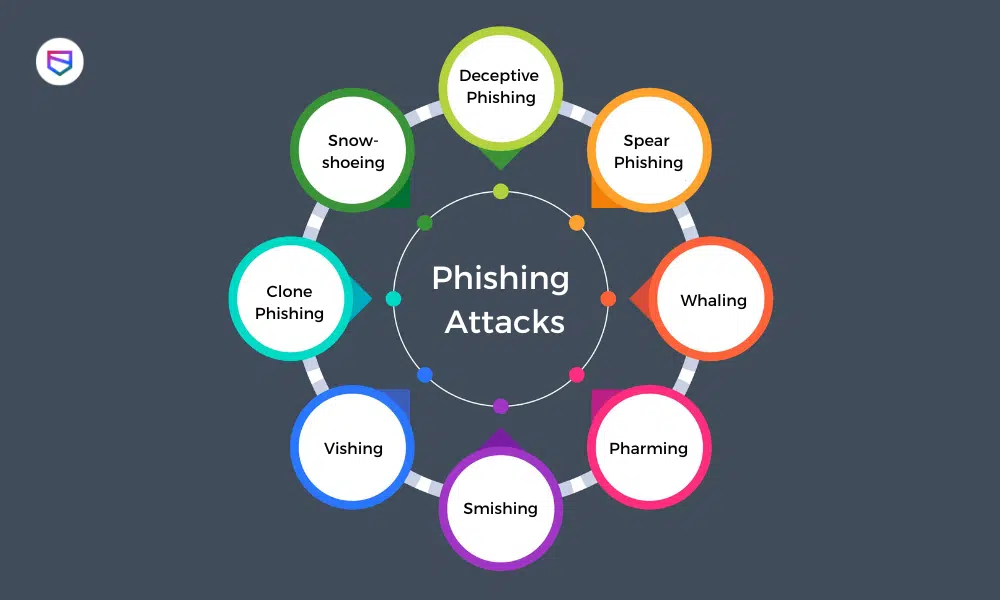
Recognizing Phishing Scams
Phishing scams represent one of the most persistent and damaging threats in the digital world. Unlike attacks that rely on complex technical exploits, phishing succeeds by manipulating human behavior – trust, urgency, fear, and routine.
As online services become central to daily life, attackers increasingly disguise themselves as banks, employers, delivery companies, or trusted platforms. Their goal is not to break systems, but to convince users to hand over access voluntarily.
Recognizing phishing scams is therefore not a technical skill, but a form of digital awareness that protects personal data, financial security, and online identity.
Understanding How Phishing Manipulates Human Behavior
Phishing attacks are built on psychological principles rather than software flaws. Attackers study how people respond to stress, authority, and perceived risk.
Messages often create a sense of urgency – claiming that an account will be suspended, a payment has failed, or suspicious activity has been detected. This pressure is intentional, reducing the likelihood that the recipient will pause and verify the information.
By mimicking familiar brands and communication styles, phishing messages bypass skepticism and exploit routine online habits.

Email Phishing: The Most Common Entry Point
Email phishing remains the most widely used method due to its low cost and massive reach. Attackers send thousands of messages, knowing that only a small percentage of responses can still lead to success.
These emails often imitate legitimate service notifications, password reset alerts, or billing confirmations. Logos, formatting, and sender names are carefully copied to appear authentic.
The danger lies not in obvious spam, but in emails that appear routine and expected, blending seamlessly into daily inbox activity.
Targeted Attacks: Spear Phishing and Personalization
Spear phishing differs from mass phishing by focusing on specific individuals or organizations. Attackers research their targets using publicly available information such as job roles, social media posts, or professional connections.
Messages may reference real colleagues, current projects, or recent events, creating a strong illusion of legitimacy. This personalization dramatically increases success rates.
Because these attacks feel relevant and familiar, they are often mistaken for genuine internal communication.
Suspicious Language and Communication Patterns
Many phishing messages reveal themselves through subtle language cues. Poor grammar, awkward phrasing, or inconsistent terminology can indicate automated or foreign-origin campaigns.
Generic greetings such as “Dear Customer” or “Dear User” often replace personalized salutations, especially in large-scale phishing attempts.
Requests for sensitive information passwords, verification codes, or payment details – should always raise concern, as legitimate organizations rarely ask for such data via email.
Malicious Links and Fake Websites
One of the most dangerous components of phishing scams is the use of deceptive links. These links lead to fake websites designed to capture login credentials or personal information.
Phishing websites often closely resemble legitimate pages, including branding, layouts, and security icons. However, the web address typically contains subtle misspellings or unusual domain extensions.
Manually typing website addresses instead of clicking links significantly reduces exposure to these attacks.

Phishing Through Text Messages and Social Platforms
Phishing is no longer limited to email. Text messages, social media platforms, and messaging apps are increasingly used to deliver malicious links and requests.
Messages may impersonate delivery services, financial institutions, or even personal contacts whose accounts have been compromised.
The informal nature of these platforms lowers suspicion, making users more likely to respond quickly.
Preventive Habits That Reduce Risk
Effective phishing prevention relies on consistent habits rather than advanced tools. Slowing down and verifying unexpected requests is one of the most powerful defenses.
Multi-factor authentication adds a critical barrier by preventing attackers from accessing accounts even if credentials are stolen.
Awareness training and regular exposure to real phishing examples strengthen long-term resistance to deceptive messages.
Responding to Suspected Phishing Attempts
When a message appears suspicious, the safest response is no response. Avoid clicking links, opening attachments, or replying directly.
Reporting phishing attempts helps service providers improve detection systems and protect other users from similar attacks.
If information has already been shared, immediate password changes and account monitoring can limit potential damage.
Conclusion
Phishing scams succeed because they exploit trust rather than technology. Recognizing these attacks requires awareness, patience, and a willingness to question unexpected messages.
By understanding phishing tactics and practicing verification, individuals can protect personal data, preserve privacy, and navigate the digital world with confidence.





Leave a Reply