-
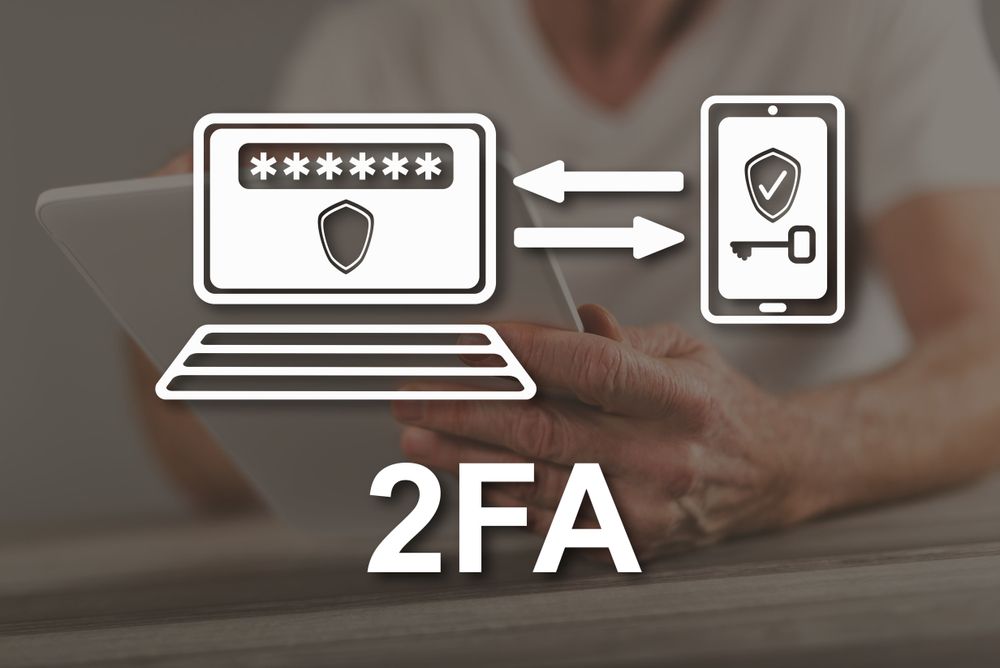
Why Two-Factor Authentication Matters
Why Two-Factor Authentication Matters Why Two-Factor Authentication Matters In today’s digital environment, cyberattacks targeting passwords and user credentials have become increasingly sophisticated. Data breaches affecting millions of accounts are now…
-

Understanding Ransomware Attacks
Understanding Ransomware Attacks Understanding Ransomware Attacks Ransomware attacks have emerged as one of the most disruptive cybersecurity threats in the modern digital landscape. Unlike attacks that quietly steal data, ransomware…
-
Cloud Storage Security Basics
Cloud Storage Security Basics Cloud Storage Security Basics Cloud storage has become a fundamental part of modern digital life. From personal photos and documents to business records and collaborative projects,…

