Why Two-Factor Authentication Matters
In today’s digital environment, cyberattacks targeting passwords and user credentials have become increasingly sophisticated. Data breaches affecting millions of accounts are now commonplace, leaving sensitive personal and organizational information at risk.
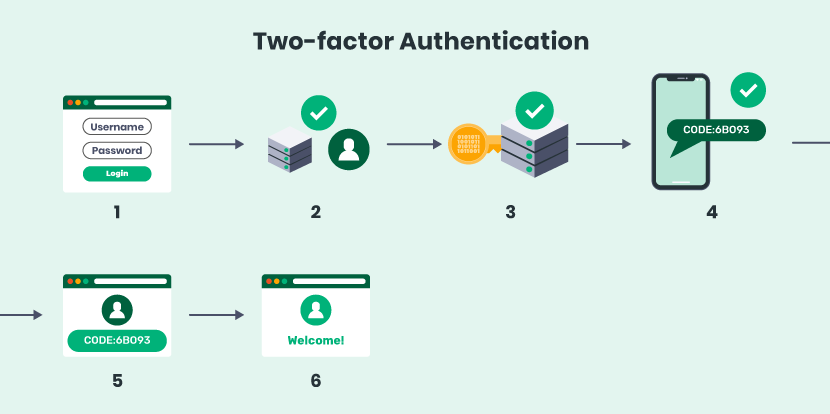
Two-Factor Authentication (2FA) provides a critical security layer beyond passwords, dramatically reducing the likelihood of unauthorized account access. It works by combining something the user knows (a password) with a second factor, which can be something the user has (a device or token) or something the user is (biometric data).
Understanding 2FA in depth allows individuals and organizations to implement robust defenses, protect critical information, and mitigate the impact of credential theft.
How Two-Factor Authentication Works: The Mechanics
Two-Factor Authentication strengthens login security by requiring two separate types of verification, which are typically categorized as:
- Knowledge factor: Something the user knows, such as a password or PIN.
- Possession factor: Something the user has, like a smartphone, hardware token, or authenticator app that generates temporary codes.
- Inherence factor: Something the user is, such as a fingerprint, facial scan, or voice recognition.
By requiring two factors from different categories, 2FA prevents attackers from gaining access with only a stolen password. Even if one factor is compromised, the second factor acts as a critical barrier.

Why Passwords Alone Are Vulnerable
Passwords are inherently fragile security tools. Users often reuse the same password across multiple services, making breaches on one platform potentially catastrophic for others. Furthermore, passwords can be stolen through phishing emails, keylogging malware, or brute-force attacks.
Even complex passwords are not immune, and sophisticated attackers employ automated systems to guess or compromise credentials. Once a password is exposed, attackers can access accounts, steal sensitive data, or impersonate the user for fraudulent activities.
Two-Factor Authentication mitigates these risks by introducing a verification step that requires access to a physical device or biometric identity, making unauthorized access exponentially more difficult.
Common Types of Two-Factor Authentication
Multiple methods of 2FA exist, each with different strengths and weaknesses:
- SMS-based codes: One-time codes sent via text message. Easy to use but vulnerable to SIM swapping attacks.
- Authenticator apps: Apps like Google Authenticator or Authy generate time-sensitive codes, independent of network security, offering improved safety.
- Hardware tokens: Physical devices that generate or store authentication codes, often used in enterprise settings for high-security access.
- Biometric verification: Fingerprints, facial recognition, or voice scans provide convenience and high security, though hardware and privacy considerations must be managed.
Enabling 2FA on Popular Platforms
Most major online services now offer 2FA. Key implementations include:
- Email: Gmail, Outlook, and Yahoo support SMS, authenticator apps, and security keys.
- Social media: Facebook, Instagram, Twitter, and LinkedIn provide optional secondary verification for logins.
- Cloud storage: Dropbox, Google Drive, and OneDrive support 2FA to protect sensitive documents and files.
Enabling 2FA generally involves accessing account settings, selecting the preferred second factor, and following a setup procedure to link the device or biometric factor.
Benefits of Two-Factor Authentication
Implementing 2FA provides multiple advantages for individuals and organizations:
- Significant reduction in account compromise: Even if passwords are stolen, attackers cannot bypass the second factor.
- Protection against phishing and credential theft: Temporary codes and device-based verification limit the effectiveness of stolen credentials.
- Improved organizational security posture: Businesses reduce risk exposure from account hijacking and insider threats.
- Peace of mind: Users gain confidence that critical accounts and sensitive data are better protected.
Best Practices for Maximizing 2FA Security
To maximize the effectiveness of 2FA:
- Prefer authenticator apps or hardware keys over SMS-based codes.
- Securely store backup codes in an offline location.
- Regularly review devices authorized to access your accounts and remove unused devices.
- Enable 2FA on all accounts that store sensitive information, especially email, financial, and cloud services.
Conclusion
Two-Factor Authentication is an essential tool for protecting digital identities and sensitive information. By requiring a second verification factor, it greatly reduces the likelihood of unauthorized account access, even when passwords are compromised.
Implementing 2FA consistently across personal and professional accounts is one of the most effective ways to enhance cybersecurity hygiene and maintain confidence in the security of online activities.




Leave a Reply