Understanding Ransomware Attacks
Ransomware attacks have emerged as one of the most disruptive cybersecurity threats in the modern digital landscape. Unlike attacks that quietly steal data, ransomware is designed to cause immediate impact by denying access to critical systems and files.
These attacks affect individuals, businesses, healthcare providers, and government institutions alike. Their effectiveness lies not in technical sophistication alone, but in the pressure they create through operational disruption and fear of data loss.
Understanding how ransomware works and how it spreads is essential for protecting devices, safeguarding data, and maintaining digital resilience.
What Is Ransomware?
Ransomware is a type of malicious software that encrypts files or locks systems, preventing legitimate access. Attackers then demand payment, typically in cryptocurrency, in exchange for restoring access.
Once ransomware executes, it systematically targets documents, databases, images, and other valuable files. Victims are presented with ransom messages that set deadlines and threaten permanent data loss.
Paying the ransom does not guarantee recovery, as attackers may fail to provide decryption keys or leave systems partially damaged.
.webp)
The Psychology Behind Ransomware Attacks
Ransomware relies heavily on psychological pressure rather than stealth. Attackers exploit urgency, fear, and the perceived value of data to force rapid decision-making.
Countdown timers, threatening language, and warnings about public data leaks are commonly used to increase stress and reduce rational evaluation of options.
This emotional manipulation often leads victims to act quickly, sometimes without consulting security professionals or exploring recovery alternatives.
Common Infection Vectors
Ransomware spreads through multiple entry points, with phishing emails being the most common. Malicious attachments or links disguise themselves as invoices, reports, or urgent notifications.
Exploited software vulnerabilities also play a major role. Unpatched operating systems and applications provide attackers with direct access to systems.
In some cases, compromised remote access services allow attackers to manually deploy ransomware across networks.
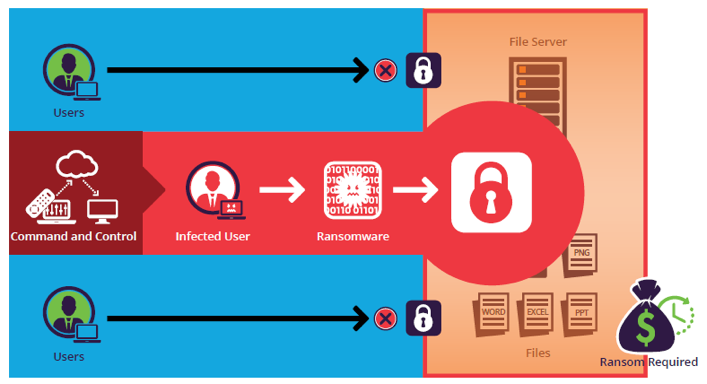
How Ransomware Spreads Within Networks
Once inside a system, ransomware often attempts to spread laterally across connected devices. Shared folders, weak credentials, and unsegmented networks accelerate this process.
Some ransomware variants actively search for backup files and attempt to delete or encrypt them, increasing the impact of the attack.
This rapid propagation can transform a single compromised device into a widespread organizational outage.
The Impact of Ransomware Attacks
The consequences of ransomware extend beyond financial loss. Downtime disrupts operations, damages reputations, and erodes trust among customers and partners.
In critical sectors such as healthcare or infrastructure, ransomware incidents can threaten safety and essential services.
Recovery efforts often require extensive technical remediation, data restoration, and system rebuilding.
Preventive Measures That Reduce Risk
Preventing ransomware relies on layered security practices. Regular software updates close vulnerabilities that attackers exploit.
Email awareness training helps users recognize suspicious messages before interacting with malicious content. Multi-factor authentication limits access even when credentials are compromised.
Network segmentation and restricted administrative privileges reduce the ability of ransomware to spread.

The Importance of Backups and Recovery Planning
Reliable backups are one of the most effective defenses against ransomware. Offline or immutable backups prevent attackers from encrypting recovery data.
Backup strategies should be tested regularly to ensure data can be restored quickly and completely.
A well-prepared recovery plan minimizes downtime and reduces pressure to pay ransoms.
Responding to a Ransomware Incident
When ransomware is detected, immediate isolation of affected systems can prevent further spread. Disconnecting from networks limits attacker control.
Incident response teams should assess damage, identify the ransomware variant, and determine whether decryption tools are available.
Transparent communication and careful decision-making are critical during recovery.
Conclusion
Ransomware attacks succeed by combining technical exploitation with psychological pressure. Their impact can be severe, but proactive security practices greatly reduce risk.
By understanding how ransomware spreads and preparing effective defenses, individuals and organizations can protect data, maintain continuity, and respond confidently to evolving threats.





Leave a Reply